



In the ever-evolving landscape of cybersecurity, the demands on security Operations Centers (SOCs) continue to grow, pushing teams to seek innovative solutions that enhance their capabilities while remaining cost-effective. As organizations wrestle with a surge in threats and the complexities of modern digital environments, a new contender has emerged that promises to revolutionize the way SOC teams operate. Enter the realm of open-source artificial intelligence (AI), a powerful tool that not only streamlines threat analysis but also offers tier-3 insights at tier-1 costs. In this article, we delve into how this transformative technology can empower SOC teams to optimize their resources, elevate their analytical prowess, and fortify their defenses against an ever-increasing tide of cyber risks. Join us as we explore the potential of open-source AI in redefining the frameworks of security analysis, making high-level expertise accessible to all.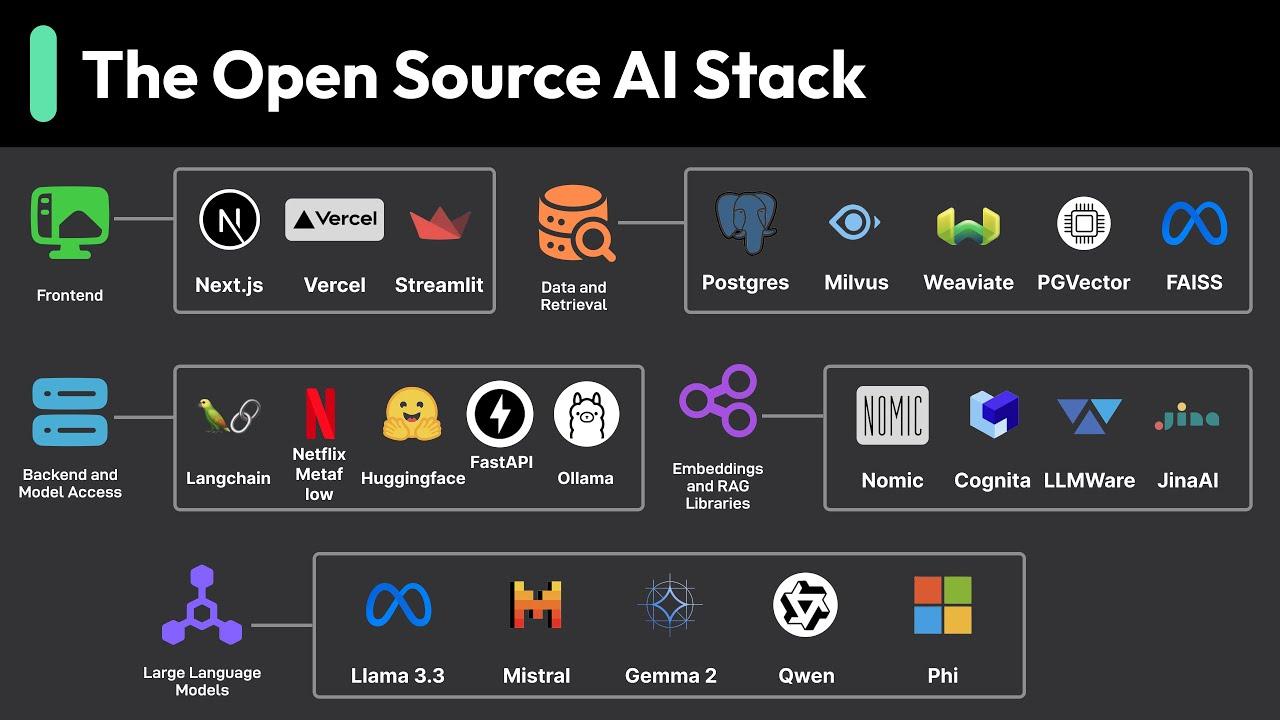
Open-source AI is quickly becoming a game-changer for Security Operations Centre (SOC) teams looking to enhance their analytical capabilities without breaking the bank. By leveraging community-driven models and tools,organizations can access powerful machine learning algorithms and data processing capabilities that were once only available through expensive proprietary solutions. This shift allows teams to perform tier-3 analysis with the resources typically associated with tier-1 services, increasing efficiency while maintaining robust security practices. Some key benefits include:
Implementing open-source AI tools can empower SOC teams to analyze vast amounts of data swiftly and effectively, thus enabling faster threat detection and response. These tools often integrate seamlessly with existing security infrastructures, providing valuable insights that can help mitigate risks and bolster overall cyber resilience. The following table outlines a comparison of traditional AI solutions versus open-source alternatives:
| Feature | Traditional AI Solutions | Open-Source AI Solutions |
|---|---|---|
| Initial Setup Cost | High | low to None |
| Customization Capability | Limited | Extensive |
| Community Engagement | Vendor-Specific | Collaborative |
| Speed of Innovation | Slow | Rapid |

Open-source AI has emerged as a game-changer in the world of cybersecurity, offering Security Operations center (SOC) teams powerful tools for extracting meaningful insights from vast amounts of data. By leveraging these advanced AI solutions, organizations can now conduct tier-3 analysis—frequently enough reserved for elite teams—without the hefty price tag typically associated with such high-level assessments.This democratization of technology allows even smaller teams to harness the capabilities of machine learning and predictive analytics, leading to more informed decision-making and faster incident responses.
One of the striking advantages of open-source AI is its ability to streamline data processing, enabling SOC teams to focus on what truly matters. The technology provides the following benefits:
| Feature | Benefit |
|---|---|
| Scalability | Easily adjust to growing data volumes. |
| Interoperability | Integrate seamlessly with existing tools. |
| User Support | Vibrant community for troubleshooting and advice. |
As SOC teams integrate open-source AI into their workflows, the transformation of raw data into actionable intelligence becomes a more manageable task. By harnessing its capabilities, teams can refine their strategies and respond to threats with newfound agility and precision, solidifying their defense mechanisms in an ever-evolving cybersecurity landscape.

as cybersecurity demands escalate, security operations center (SOC) teams face mounting pressure to deliver swift and effective threat analysis without breaking the bank. By harnessing the power of open-source tools, organizations can optimize their resources while achieving remarkable analysis capabilities. These tools not only reduce costs considerably but also allow for greater flexibility and customization, empowering teams to tailor their workflows according to specific operational requirements. Some key benefits include:
To further capitalize on these advantages, SOC teams should consider integrating open-source AI solutions specifically designed for advanced analytics. For example, implementing machine learning algorithms to streamline data processing can yield faster insights on potential threats, facilitating a proactive rather than reactive approach. Below is a concise comparison of popular open-source tools suited for tier-3 analysis, highlighting their key features:
| Tool | Key Feature | Use Case |
|---|---|---|
| OSSEC | Log Analysis | Real-time intrusion detection |
| ELK Stack | Data Visualization | Centralized logging and analysis |
| Snort | Network Monitoring | Packet analysis and threat detection |

Implementing open-source AI solutions in a Security Operations Center (SOC) can radically transform operations,enhancing efficiency and reducing costs. by leveraging community-driven technologies,teams can access advanced analytics without the burden of exorbitant licensing fees. Key aspects to consider include:
A collaborative approach is also essential for prosperous implementation. Engaging with the open-source community can provide valuable insights and support. Consider the following strategies for collaboration:
the emergence of open-source AI solutions presents a transformative opportunity for Security Operations Center (SOC) teams seeking to enhance their analytical capabilities without straining their budgets. By harnessing these innovative tools, organizations can achieve tier-3 analysis with the efficiency and depth typically reserved for tier-1 services.this dual benefit not only promotes cost-effectiveness but also empowers security analysts to focus on higher-level strategic initiatives, thereby strengthening overall cybersecurity posture. As the landscape of cyber threats evolves, embracing open-source AI could be the key to staying ahead of the curve—ensuring that SOC teams are equipped to tackle challenges with the ingenuity and precision required in today’s fast-paced digital world. the future of cybersecurity is here; it’s open-source, it’s intelligent, and it invites you to explore its potential.